What Do You Need On Computer To Watch And Record Secirty Cameras
What is Computer Security? Introduction to Computer Security
Terminal updated on Dec 29,2021 86.1K Views
The Internet has transformed our lives in many good ways. Unfortunately, this vast network and its associated technologies also have brought in their wake, the increasing number of security threats. The most effective way to protect yourself from these threats and attacks is to be enlightened of standard cybersecurity practices. This article on "What is Computer Security?" presents an introduction to estimator security and its primal concepts.
- What is Computer Security?
- Computer Security Threats
- Why is reckoner security important?
- Best computer security practices.
What is computer security?
Figurer security basically isthe protection of computer systems and information from harm, theft, and unauthorized use. Information technology is the process of preventing and detecting unauthorized use of your estimator system.
In that location are various types of reckoner security which is widely used to protect the valuable data of an arrangement.
What is Computer Security and its types?
One mode to ascertain the similarities and differences amidst Computer Security is past asking what is beingness secured. For instance,
- Data security is securing information from unauthorized access, modification & deletion
- Application Security is securing an application by edifice security features to prevent from Cyber Threats such equally SQL injection, DoS attacks, data breaches and etc.
- Computer Security ways securing a standalone machine by keeping information technology updated and patched
- Network Security is past securing both the software and hardware technologies
- Cybersecurity is defined as protecting calculator systems, which communicate over the computer networks
It's important to understand the distinction between these words, though in that location isn't necessarily a clear consensus on the meanings and the degree to which they overlap or are interchangeable.
So, Computer security tin be divers as controls that are put in place to provide confidentiality, integrity, and availability for all components of computer systems. Let's elaborate the definition.
Components of calculator system
The components of a calculator system that needs to be protected are:
- Hardware, the physical role of the reckoner, like the system retentiveness and disk drive
- Firmware,permanent software that is etched into a hardware device'southward nonvolatile memory and is mostly invisible to the user
- Software,the programming that offers services, like operating system, word processor, internet browser to the user
The CIA Triad
Calculator security is mainly concerned with iii main areas:
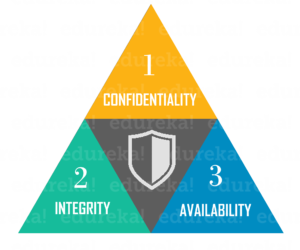
- Confidentiality is ensuring that information is available only to the intended audience
- Integrity is protecting data from being modified by unauthorized parties
- Availability isprotecting data from existence modified by unauthorized parties
In simple language, figurer security is making sure data and computer components are usable but still protected from people or software that shouldn't access information technology or modify it.
Now moving frontwards with this 'What is Computer Security?" article let's look at the nearly common security threats.
Computer security threats
Computer security threats are possible dangers that can maybe hamper the normal functioning of your computer. In the present historic period, cyber threats are constantly increasing equally the world is going digital. The almost harmful types of computer security are:
Viruses
 A computer virus is a malicious program which is loaded into the user'southward computer without user'south cognition. It replicates itself and infects the files and programs on the user's PC. The ultimate goal of a virus is to ensure that the victim'due south calculator volition never exist able to operate properly or fifty-fifty at all.
A computer virus is a malicious program which is loaded into the user'southward computer without user'south cognition. It replicates itself and infects the files and programs on the user's PC. The ultimate goal of a virus is to ensure that the victim'due south calculator volition never exist able to operate properly or fifty-fifty at all.
Estimator Worm
 A reckoner worm is a software program that can copy itself from ane computer to some other, without human interaction. The potential risk here is that it will use up your calculator hard disk space because a worm tin replicate in greate book and with great speed.
A reckoner worm is a software program that can copy itself from ane computer to some other, without human interaction. The potential risk here is that it will use up your calculator hard disk space because a worm tin replicate in greate book and with great speed.
Phishing

Disguising every bit a trustworthy person or business organization, phishers effort to steal sensitive financial or personal information through fraudulent e-mail or instant messages. Phishing in unfortunately very easy to execute. You lot are deluded into thinking information technology's the legitimate mail and you may enter your personal information.
Botnet
 A botnet is a grouping of computers connected to the internet, that have been compromised by a hacker using a computer virus. An individual calculator is called 'zombie figurer'. The result of this threat is the victim's computer, which is the bot will be used for malicious activities and for a larger scale attack similar DDoS.
A botnet is a grouping of computers connected to the internet, that have been compromised by a hacker using a computer virus. An individual calculator is called 'zombie figurer'. The result of this threat is the victim's computer, which is the bot will be used for malicious activities and for a larger scale attack similar DDoS.
Rootkit
 A rootkit is a reckoner program designed to provide continued privileged access to a computer while actively hiding its presence. One time a rootkit has been installed, the controller of the rootkit volition be able to remotely execute files and change system configurations on the host machine.
A rootkit is a reckoner program designed to provide continued privileged access to a computer while actively hiding its presence. One time a rootkit has been installed, the controller of the rootkit volition be able to remotely execute files and change system configurations on the host machine.
Keylogger
 Also known equally a keystroke logger, keyloggers can track the real-time activity of a user on his estimator. It keeps a record of all the keystrokes made past user keyboard. Keylogger is also a very powerful threat to steal people's login credential such equally username and countersign.
Also known equally a keystroke logger, keyloggers can track the real-time activity of a user on his estimator. It keeps a record of all the keystrokes made past user keyboard. Keylogger is also a very powerful threat to steal people's login credential such equally username and countersign.
These are maybe the most mutual security threats that you lot'll come up across. Apart from these, there are others like spyware, wabbits, scareware, bluesnarfing and many more than. Fortunately, there are means to protect yourself against these attacks.
Why is Computer Security Important?
In this digital era, we all want to keep our computers and our personal data secure and hence computer security is important to keep our personal information protected. It is also important to maintain our computer security and its overall wellness by preventing viruses and malware which would affect on the system functioning.
Computer Security Practices
Reckoner security threats are becoming relentlessly inventive these days. There is much need for one to arm oneself with information and resources to safeguard confronting these complex and growing computer security threats and stay safe online. Some preventive steps y'all can take include:
- Secure your computer physically past:
- Installing reliable, reputable security and anti-virus software
- Activating your firewall, because a firewall acts as a security guard betwixt the net and your local area network
- Stay upwards-to-date on the latest software and news surrounding your devices and perform software updates as soon as they go available
- Avoid clicking on email attachments unless you know the source
- Change passwords regularly, using a unique combination of numbers, messages and case types
- Use the internet with caution and ignore popular-ups, drive-by downloads while surfing
- Taking the fourth dimension to research the basic aspects of reckoner security and educate yourself on evolving cyber-threats
- Perform daily full organization scans and create a periodic system backup schedule to ensure your data is retrievable should something happen to your calculator.
Apart from these, there are many ways y'all can protect your computer organization. Aspects such as encryption and reckoner cleaners can aid in protecting your computers and its files.
Unfortunately, the number of cyber threats are increasing at a rapid step and more sophisticated attacks are emerging. And so, having a good foundation in cybersecurity concepts will allow you lot to protect your computer confronting ever-evolving cyber threats.
If you lot wish to learn cybersecurity and build a colorful career in cybersecurity, then bank check out ourCybersecurity Certification Grooming which comes with instructor-led alive preparation and real-life project experience. This preparation will help you understand cybersecurity in depth and assist you reach mastery over the subject.
You can besides accept a look at our newly launched course onCompTIA Security+ Certification which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Learn Cybersecurity the right way with Edureka'south masters in cyber security plan and defend the world's biggest companies from phishers, hackers and cyber attacks.
Got a question for us? Delight mention it in the comments department of "What is Computer Security?" and we volition get back to y'all.
Source: https://www.edureka.co/blog/what-is-computer-security/
Posted by: russotookents.blogspot.com


0 Response to "What Do You Need On Computer To Watch And Record Secirty Cameras"
Post a Comment